Jinn
Automated Server Security & Vulnerability Patching Platform
80%
Less Manual Work
100%
On-Premise
<24h
Patch Deployment
✓ No software installation
✓ Pure SSH connection
✓ Reduced attack surface
✓ Complete data control

TRUSTED BY 500+ ENTERPRISES ACROSS THE GULF REGION & BEYOND
Automated Patch Management ROI Calculator
See how much time and money automated vulnerability scanning and patching saves your IT department
Without Jinn
With Jinn
Save $121,500 /year
Save more than $10,125 /month with Jinn
Plus improved security posture and compliance readiness
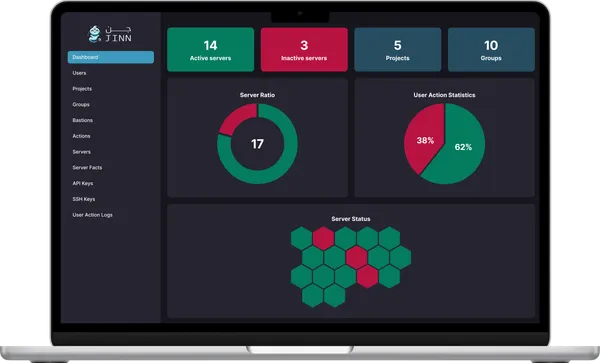
Security Dashboard for IT Managers: Real-Time Vulnerability Tracking
Get instant visibility into infrastructure health without
technical complexity.
Traffic light system:
Green = Secure ,
Yellow = Attention Needed ,
Red = Urgent
Real-Time Security Dashboard
Monitor all servers at a glance. No technical knowledge required—just clear, actionable insights.
- • CVE exposure tracking
- • Patch compliance status
- • Security score trending
Automated Compliance Reports
Generate audit-ready documentation in seconds, not days. Ready for ISO, SOC2, and GDPR audits.
- • One-click report generation
- • Historical audit trail
- • Compliance score tracking
Risk Reduction Metrics
Quantify security improvements with clear KPIs for board presentations and stakeholder reports.
- • Mean time to patch (MTTP)
- • Vulnerability remediation rate
- • Security posture score
"Jinn's automated vulnerability scanning and patching reduced our security incident response time from days to hours. The executive dashboard gives me confidence to report our security posture to the board without relying on technical staff for translation. Best ROI of any security tool we've deployed."
— Rashid A., IT Security Director
Gulf Region Financial Services • 1,200+ servers managed
Infrastructure Security Management for DevOps & SRE Teams
Built by engineers, for engineers. Automate routine tasks and focus on strategic initiatives.
Server Inventory Management & Asset Discovery
Maintain comprehensive visibility of all servers, VMs, and bastion hosts with automated asset discovery and centralized inventory tracking.
Agentless Deployment - Zero Installation
No software to install on your servers. Pure SSH connections reduce attack surface and eliminate agent-related vulnerabilities—deploy patches and configurations securely without any footprint.
Automated Security Hardening & CIS Benchmarks
Apply SSH, kernel, and system hardening policies automatically to maintain security standards and achieve CIS compliance.
Zero-Downtime Patch Deployment
Schedule updates during maintenance windows with automated rollback capabilities and zero-downtime deployment strategies.
Multi-Cloud & Hybrid Infrastructure Support
Unified management for Linux, BSD, AWS, Azure, GCP, and on-premise environments—one platform for all your infrastructure.
Compliance Audit Trail & Reporting
Complete logging of all actions with detailed attribution for accountability, regulatory compliance, and audit-ready documentation.
Open Source Commitment
Explore InfraNinja — our open-source infrastructure automation library. Available as a standalone solution or integrated within Jinn.
View InfraNinja on GitHubRole-Based Access Control
Three roles, three levels of power. Everyone gets what they need, nothing they don't.
Admins
Full system access. Configure policies, manage users, and control everything.
Managers
View dashboards, generate reports, and monitor infrastructure health.
Engineers
Deploy patches, manage inventory, and maintain operational excellence.
On-Premise Security Platform: Complete Control & Data Sovereignty
Complete Control & Data Sovereignty
Offline CVE Vulnerability Scanning
Complete CVE vulnerability detection without internet connectivity. Maintain up-to-date CVE database via secure offline transfer for air-gapped environments.
100% On-Premise Deployment
All components run within your network. Zero cloud dependencies. Your data never leaves your infrastructure.
Air-Gap Compatible
Designed for the most secure environments. Operates completely disconnected from external networks.
Agentless Architecture - Zero Software Installation
No agents, no software to install or maintain. Pure SSH connection only—reducing attack surface and eliminating agent vulnerabilities. Minimal footprint, maximum security.
Built for the Gulf Region
Native Arabic and English interface designed for GCC enterprises. Full right-to-left (RTL) support with culturally-appropriate UI/UX.
Docker Compose Deployment
Self-hosted with simple Docker Compose deployment. Just one VM required—no complex infrastructure or cloud platform dependencies.
Direct Cloud Integration
Seamless integration with cloud provider inventories: AWS, GCP, Azure, VMware, and Nutanix—automatically discover and manage your assets.
Model Context Protocol (MCP) Integration
Jinn features native integration with the Model Context Protocol (MCP), enabling AI-powered infrastructure management and intelligent automation. Through MCP, Jinn can provide contextual infrastructure data to AI assistants, allowing for natural language queries, automated problem diagnosis, and intelligent remediation suggestions.
AI-Assisted Operations
Query your infrastructure status, analyze trends, and receive recommendations through natural language interactions powered by MCP.
Intelligent Automation
Leverage AI-driven insights to automate complex decision-making processes and optimize infrastructure management workflows.
Jinn vs. Tenable, Nessus, OpenVAS: Comparison
Enterprise security with automated patching—not just scanning
| Feature | Jinn | Tenable/Nessus | OpenVAS | Manual Process |
|---|---|---|---|---|
| Setup Time | < 1 day | 1-2 weeks | 2-4 weeks | N/A |
| Automated Patching | ✓ | ✗ | ✗ | ✗ |
| Configuration Hardening | ✓ | ~ | ✗ | ✗ |
| Compliance Reports | ✓ | ✓ | ~ | ✗ |
| User-Friendly Dashboard | ✓ | ~ | ✗ | ✗ |
| Price (100 servers) | Contact us | $$$$$ | Free (DIY) | Staff cost |
| 24/7 Support | ✓ | ~ | ✗ | ✗ |
Why 500+ Enterprises Trust Jinn for Server Security
From Dubai-based startups to major GCC enterprises, organizations across the Gulf region rely on Jinn to automate vulnerability management and reduce security risk.
Complete Security Platform
Unlike vulnerability scanners that only identify problems, Jinn automatically fixes them. Continuous scanning, automated patching, configuration hardening, and compliance reporting—all in one platform.
"The only tool where we both find and fix vulnerabilities without switching platforms." — Ahmed A., DevOps Lead, Healthcare Provider
Built by Security Experts
Developed by Kalvad's specialized security engineering team with decades of combined infrastructure experience. Battle-tested across GCC financial services, healthcare, government, and enterprise environments.
"You can tell this was built by people who actually manage servers, not just scan them." — Fatima A., Senior SRE, E-commerce Platform
White-Glove Support
Dedicated technical account manager, 24/7 emergency response, and proactive health monitoring. We don't just provide software—we partner in your security operations.
"Support responds in minutes, not days. They helped us customize policies for our unique compliance needs." — Mohammed A., CISO, Manufacturing Enterprise
Production-Ready in Hours
Most customers are fully operational within 48 hours. With zero software installation and agentless architecture, pre-built security policies, and intelligent defaults mean you're protected immediately, not eventually.
"Went from signup to scanning 800 servers in under 2 days. Our previous tool took 3 months to configure." — Khalid A., Infrastructure Manager, SaaS Company
Enterprise-Grade Security & Trust
Zero-Trust Architecture
End-to-end encryption, least-privilege access, and continuous verification for every action.
Compliance Ready
ISO 27001, SOC 2 Type II certified. Data residency, HIPAA, and PCI-DSS compliant deployments available for GCC region.
Data Sovereignty
Self-hosted option ensures your data never leaves your infrastructure. You maintain complete control.
Security Guarantees
Frequently Asked Questions
How quickly can we get started?
Most organizations are scanning their first servers within 24 hours. Since Jinn is agentless with zero software installation, setup is instant—just provide SSH access. Start with a small pilot group before scaling enterprise-wide.
Do you support hybrid cloud and on-premise environments?
Yes. Jinn works seamlessly across AWS, Azure, GCP, private clouds, and bare-metal servers. The same management interface for all your infrastructure, regardless of where it lives.
Can I try Jinn before purchasing?
Yes! Book a personalized demo where we'll walk you through the platform using your infrastructure requirements. Our team will show you exactly how Jinn addresses your specific security challenges.
How does pricing work?
Simple per-server pricing with volume discounts. No hidden fees, no per-user charges. Annual contracts include dedicated support and guaranteed SLA. Contact us for a custom quote based on your infrastructure size.
Is our data safe? Where is it stored?
Your infrastructure data is encrypted at rest and in transit. Self-hosted deployment ensures data never leaves your network and remains within UAE/GCC jurisdiction, meeting local data residency requirements. We never sell or share customer data.
What if we need custom integration or compliance requirements?
Our professional services team specializes in custom integrations with SIEM, ticketing systems, and compliance frameworks. We've successfully deployed in highly regulated GCC industries including banking, healthcare, government entities, and critical infrastructure.
Automate Server Security & Reduce Vulnerabilities by 80%
Enterprise-grade infrastructure security with complete control. Self-hosted deployment, maintain data sovereignty, and eliminate vulnerabilities automatically. No cloud dependencies required.
500+
Enterprises
100K+
Servers Protected
Self-Hosted
Complete Control